Counterfeit Electronics in the DOD Supply Chain
Counterfeit semiconductor devices entering the Department of Defense (DOD) supply chain continue to pose risks to many of our country’s most sophisticated aerospace and defense systems. However, considerable progress is being made by the DOD, industry and academia in developing approaches to help eliminate these devices before they are put into critical systems.
Supply and Demand

The demand side of this market exists because many of the DOD’s most sophisticated systems have product lifetimes that far exceed the lifetime of a typical commercial semiconductor device. Defense systems can have useful lifetimes of 30 years or more and can be prohibitively expensive to redesign and requalify. Meanwhile, commercial semiconductor production is dominated by devices intended for the consumer electronics market, where lifetimes can be as short as 3-5 years. With a nearly unlimited and inexpensive supply of obsolete semiconductor devices in the world and a DOD long term demand for these same obsolete semiconductors, the counterfeiters will find a way to bring that supply and demand into balance.
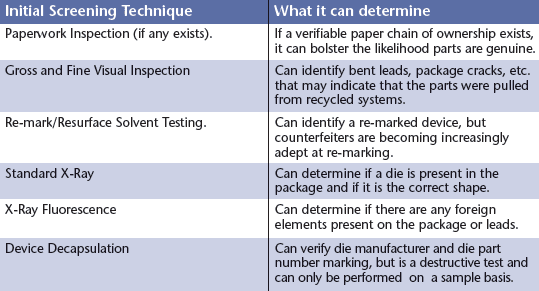
As good as these techniques have been at catching the initial waves of counterfeits, the counterfeiters continue to develop more refined and difficult to detect counterfeits. In particular, the counterfeiter’s ability to remark devices has become so good that it can be impossible to differentiate them from an authentic device.
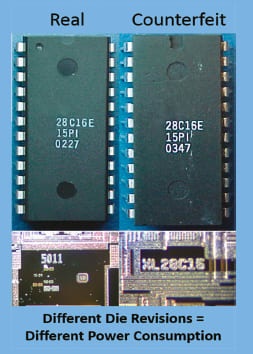
Today’s more sophisticated counterfeits are taking advantage of the fact that many semiconductor devices come from families of devices derived from the identical die design. For instance, a single microprocessor design will typically yield a range of performance characteristics as a natural consequence of the variability of the underlying wafer fabrication process upon which it is built. The manufacturer will test these devices and “grade” them according to their performance characteristics such as speed and functionality over temperature.
The parts are marked according to this grading process and sold into different applications for different prices. For instance, a slower speed device could be sold to a consumer electronics manufacturer for five dollars, while a high speed device may be sold to an Air Force contractor for a high performance application for twenty-five dollars. All that is needed to create a very difficult to detect counterfeit is to re-mark the poorer performing device as the higher performing one. Re-marking, as stated above, is one process the counterfeiters are getting very good at. Since both of these parts have the exact same die in them and come in the same package, the traditional counterfeit detection techniques of Table 1 will not be able detect them.
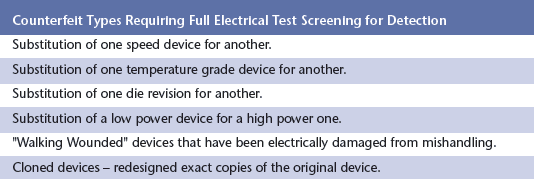
The only way to reliably screen these more sophisticated counterfeits is to perform full electrical testing across the device’s entire specified temperature range. This is the same type of testing the original manufacturer performed and will be able to verify the “grading” marked on the device. Table 2 lists some of these more sophisticated counterfeit types that require full electrical testing to detect.
Clones and Trojans
Another particularly difficult to detect counterfeit device type from Table 2 is the “Clone.” A cloned device is one that is actually redesigned and remanufactured using todays semiconductor technology in order to meet the original manufacturer’s performance specifications. By using current semiconductor technology, these cloned devices often perform much faster and with more device operating margin than the original device. The only way to catch these devices is to perform full electrical testing over the entire operating temperature range, as discussed previously, but in this case take the testing one step further. Instead of only testing to make sure it at least meets its performance specs, the actual device performance must be measured to see if it statistically exceeds its performance specification. This actual performance testing will determine if the device is ‘too good” and is, therefore, a potential counterfeit.
When discussing clones, the question is inevitably asked that if a cloned device has even better electrical performance than the original device, why can’t it just be used in place of the original? The answer is that while it is relatively easy to redesign a simple device to electrically function like an old one, it is much more difficult to make that new device with the same quality and reliability as the original manufacturer. Remember that the counterfeiters are out to make money by doing as little as possible to get someone to buy parts and are not likely to employ the same rigorous military qualification processes over the entire operating temperature range that the original manufacturer did.
Trojans, if designed well, can be extremely difficult to detect. Today, there are no commercially available ways to assure your device doesn’t contain a Trojan. On the other hand, a good Trojan is even more difficult to engineer than a Clone, so it is less likely that the older, common industry devices (that make up the bulk of today’s counterfeit devices) would include a Trojan.
But as the counterfeit device supply issue moves from the hands of relatively unsophisticated e-waste recyclers and into the hands of establishments or governments with malicious intent, the resources and desire to create Trojans increases significantly. This is compounded by the fact that most new semiconductor fabrication is done outside the United States where designs and mask sets could be more easily compromised to introduce Trojans.
One solution to limiting the Trojan threat is to use the DOD Defense Microelectronics Activity (DMEA) “Trusted” source program. This program accredits US based semiconductor manufacturing locations that have proven high level security processes and procedures in place. Numerous other solutions are being studied by the DOD and academia, but so far none of the published approaches can be considered a universally viable solution.
There is some good news in the industry when it comes to identifying and eliminating counterfeit semiconductor threats. There is a growing awareness in the industry with an abundance of technical conferences and papers proposing solutions. Academic institutions are studying techniques to guarantee newly fabricated devices can be authenticated. Finally the DOD is sponsoring defense industry research programs in numerous counterfeit related areas.
One such program is sponsored by the Missile Defense Agency (MDA) and targets the development of new and more effective counterfeit screening techniques for Field Programmable Gate Arrays (FPGA’s). FPGA’s are used extensively in the defense industry because of their flexibility and wide range of available functions. They are often the “brains” of the system they are designed into, where failures caused by counterfeit devices could lead to catastrophic consequences.
Another is DARPA’s Supply Chain Hardware Integrity for Electronics Defense (SHIELD) program. The goal of DARPA’s SHIELD program is to eliminate counterfeit integrated circuits from the electronics supply chain by making counterfeiting too complex and time-consuming to be cost-effective. SHIELD aims to combine NSA-level encryption, sensors, near-field power and communications into a microscopic-scale chip capable of being inserted into the packaging of an integrated circuit.
Although the industry is doing much more to thwart the incursion of counterfeit semiconductors into the DOD supply chain than ever before, there is no realistic end in sight. Continued diligence is required in employing the initially developed mechanical counterfeit detection techniques as well as the even more effective comprehensive electrical test techniques. The counterfeiters will be relentless – it will take the combined efforts of the DOD, academia, the original semiconductor manufacturers and independent test labs to ultimately bring this threat under control.
This article was written by Joseph L Holt, Vice President, Integra Technologies LLC (Wichita, KS). For more information, Click Here .
Top Stories
INSIDERManufacturing & Prototyping
![]() How Airbus is Using w-DED to 3D Print Larger Titanium Airplane Parts
How Airbus is Using w-DED to 3D Print Larger Titanium Airplane Parts
INSIDERManned Systems
![]() FAA to Replace Aging Network of Ground-Based Radars
FAA to Replace Aging Network of Ground-Based Radars
NewsTransportation
![]() CES 2026: Bosch is Ready to Bring AI to Your (Likely ICE-powered) Vehicle
CES 2026: Bosch is Ready to Bring AI to Your (Likely ICE-powered) Vehicle
NewsSoftware
![]() Accelerating Down the Road to Autonomy
Accelerating Down the Road to Autonomy
EditorialDesign
![]() DarkSky One Wants to Make the World a Darker Place
DarkSky One Wants to Make the World a Darker Place
INSIDERMaterials
![]() Can This Self-Healing Composite Make Airplane and Spacecraft Components Last...
Can This Self-Healing Composite Make Airplane and Spacecraft Components Last...
Webcasts
Defense
![]() How Sift's Unified Observability Platform Accelerates Drone Innovation
How Sift's Unified Observability Platform Accelerates Drone Innovation
Automotive
![]() E/E Architecture Redefined: Building Smarter, Safer, and Scalable...
E/E Architecture Redefined: Building Smarter, Safer, and Scalable...
Power
![]() Hydrogen Engines Are Heating Up for Heavy Duty
Hydrogen Engines Are Heating Up for Heavy Duty
Electronics & Computers
![]() Advantages of Smart Power Distribution Unit Design for Automotive...
Advantages of Smart Power Distribution Unit Design for Automotive...
Unmanned Systems
![]() Quiet, Please: NVH Improvement Opportunities in the Early Design...
Quiet, Please: NVH Improvement Opportunities in the Early Design...


































