Considering Software Protection for Embedded Systems
Reconfigurable embedded systems can be subject to tamper methods applicable to software.
Given the current trend of reprogrammable embedded devices within the Department of Defense and industry, attention needs to be refocused on the benefits or measurability of software protection applied to this domain. Modern reconfigurable embedded systems consider circuits as software and the tamper methods applicable to physical circuits as new threats to a broadened definition of software. In the traditional sense, software referred to the bits (1s and 0s) representing language statements that could be executed on hardware processors. Today, embedded systems utilizing field-programmable gate arrays (FPGAs) realize circuits merely by downloading a sequence of bits that instantiate gates, controllers, arithmetic logic units, crypto circuits, and even processors. Thus, a circuit implemented on embedded systems utilizing an FPGA is essentially software.
Considering the proliferation of embedded systems with reprogrammable hardware components in both commercial and military sectors, one can show the impact of malicious activity geared to reverse-engineer, tamper, or copy critical technologies residing in those systems.
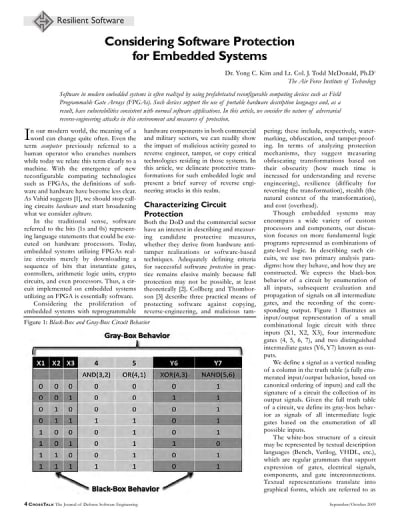
The semantics (or black-box behavior) of a circuit consist of only the input and
output signal pairs. Intuitively, one way to think of circuit protection is the act of hiding all intermediate transitions that transform input to output. The collection of these transitions, in essence, represents the intellectual property of a circuit. Without knowledge of the original intermediate transitions, no human or automated process may derive other information about the original circuit such as topology, signal definitions, or component definitions.
To protect a circuit, one can replace the original circuit with a semantically equivalent version (one which does the same function) that hides the intellectual property of the original in some definable or measurable way. This formulation restates the essence of a virtual “black box” because it defines full protection as a replacement circuit that does not leak any more information relative to an original circuit (other than its input/output characteristics). In more practical settings, the goal of using a replacement circuit becomes obscuring the original circuit in some way so that the cost of reverse engineering is maximized, while operation characteristics of the circuit are not degraded beyond an acceptable level.
There are a number of different ways to discover and alter the functionality of a circuit. The term “tampering” refers to broad categories of circuit exploitation, including subversion, modification, and reverse engineering. Reverse engineers typically target reproduction of a circuit’s functionality, usually for capital gain or malicious intent. Specific attacks can be roughly categorized as brute force, white box/gray box, side-channel, and fault-injection.
Fault injection is a generic term describing the injection of faults into digital systems using a variety of attacks — raising voltage higher or lower than system tolerances, inducing voltage spikes, or introducing clock glitches. An adversary may use fault injections with realized circuits in order to reduce encryption strength via key-space reduction. This exploit requires internal circuit access and reduces the goal of the adversary from using brute-force methods to interrupt the successful encryption/decryption process itself.
This work was done by Yong C. Kim and Lt. Col. J. Todd McDonald of the Air Force Institute of Technology. For more information, download the Technical Support Package (free white paper) at www.defensetechbriefs.com/tsp under the Information Sciences category. AFRL-0145
This Brief includes a Technical Support Package (TSP).
Considering Software Protection for Embedded Systems
(reference AFRL-0145) is currently available for download from the TSP library.
Don't have an account?
Overview
The document discusses the evolving definitions of software and hardware in the context of modern embedded systems, particularly focusing on reconfigurable computing technologies such as Field Programmable Gate Arrays (FPGAs). Traditionally, software was defined as the binary code executed on hardware processors. However, with the advent of FPGAs, circuits can now be realized by downloading sequences of bits that instantiate various components, blurring the lines between hardware and software. This shift necessitates a broader understanding of software, as circuits implemented on FPGAs can be considered a form of software.
The document emphasizes the vulnerabilities associated with embedded systems, especially in commercial and military applications. It highlights the risks of malicious activities aimed at reverse engineering, tampering, or copying critical technologies within these systems. To address these threats, the authors propose protective transformations for embedded logic and provide a brief overview of reverse engineering attacks.
The authors reference the work of Collberg and Thomborson, who identify three primary methods for protecting software: watermarking, obfuscation, and tamper-proofing. These methods aim to prevent copying, reverse engineering, and malicious tampering. The document discusses the challenges in defining successful software protection criteria, noting that achieving full protection may be theoretically impossible. It suggests that protective measures should be evaluated based on their obscurity, resilience, stealth, and cost.
In analyzing circuits, the document distinguishes between different paradigms: black-box behavior, gray-box behavior, and white-box structure. Black-box behavior refers to the input/output representation of a circuit, while gray-box behavior involves understanding the signals of intermediate logic gates. The white-box structure is represented through textual description languages like Verilog and VHDL, which facilitate the expression of gates and their interconnections.
Overall, the document underscores the importance of developing robust protective measures for embedded systems in light of their increasing complexity and the potential for adversarial attacks. It calls for a reevaluation of traditional definitions and approaches to software and hardware, advocating for a more integrated perspective that reflects the realities of modern computing technologies.
Top Stories
INSIDERDesign
![]() How Airbus is Using w-DED to 3D Print Larger Titanium Airplane Parts
How Airbus is Using w-DED to 3D Print Larger Titanium Airplane Parts
NewsSensors/Data Acquisition
![]() Microvision Aquires Luminar, Plans Relationship Restoration, Multi-industry Push
Microvision Aquires Luminar, Plans Relationship Restoration, Multi-industry Push
INSIDERManned Systems
![]() A Next Generation Helmet System for Navy Pilots
A Next Generation Helmet System for Navy Pilots
NewsAR/AI
![]() Accelerating Down the Road to Autonomy
Accelerating Down the Road to Autonomy
INSIDERDefense
![]() New Raytheon and Lockheed Martin Agreements Expand Missile Defense Production
New Raytheon and Lockheed Martin Agreements Expand Missile Defense Production
ArticlesAR/AI
![]() CES 2026: Bosch is Ready to Bring AI to Your (Likely ICE-powered) Vehicle
CES 2026: Bosch is Ready to Bring AI to Your (Likely ICE-powered) Vehicle
Webcasts
Semiconductors & ICs
![]() Advantages of Smart Power Distribution Unit Design for Automotive...
Advantages of Smart Power Distribution Unit Design for Automotive...
Unmanned Systems
![]() Quiet, Please: NVH Improvement Opportunities in the Early Design...
Quiet, Please: NVH Improvement Opportunities in the Early Design...
Electronics & Computers
![]() Cooling a New Generation of Aerospace and Defense Embedded...
Cooling a New Generation of Aerospace and Defense Embedded...
Automotive
![]() Battery Abuse Testing: Pushing to Failure
Battery Abuse Testing: Pushing to Failure
Transportation
![]() A FREE Two-Day Event Dedicated to Connected Mobility
A FREE Two-Day Event Dedicated to Connected Mobility