FPGA-Based System for Tracking Digital Information Transmitted Via Peer-to-Peer Protocols
The FPGA-based system tracks illicit dissemination of sensitive government information.
Peer-to-peer (P2P) networking has changed the way users search for, send, and receive digital information over the Internet. Instead of relying on interactions with centralized servers to upload and download digital content, users now share content directly with other users. While peer-to-peer networking provides new and powerful applications for the legitimate distribution of digital information, it is also being used for many illicit purposes as well.
The goal of this research is to develop a system for detecting and tracking the illicit dissemination of sensitive government information using file sharing applications within a target network, and tracking terrorist cells or criminal organizations that are covertly communicating using VoIP applications.
Results show that the FPGA tool processes peer-to-peer packets of interest 92% faster than a software-only configuration and is 99% accurate at capturing and processing BitTorrent Handshake messages under a network traffic load of at least 89.6 Mbps. When SIP is added to the system, the probability of intercept for BitTorrent Handshake messages remains at 99% and the probability of intercept for SIP control packets is 97.6% under a network traffic load of at least 89.6 Mbps, demonstrating that the tool can be expanded to process additional peer-to-peer protocols with minimal impact on overall performance.
This research provides the Air Force and other government agencies with a unique method of detecting and tracking both illicit file sharing and VoIP phone call patterns. This system differs from other methods of tracking illicit file sharing in that it is completely passive, meaning the system transmits absolutely no information into the network being monitored, making it completely invisible to users of the network.
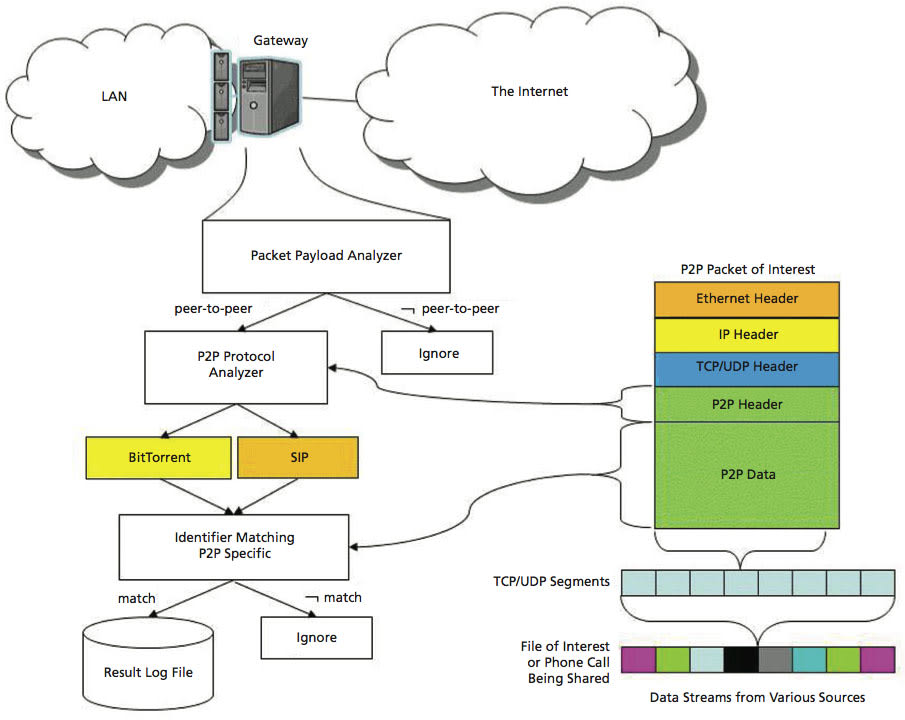
The TRacking and Analysis for Peer-to-Peer (TRAPP) system allows an investigator or system administrator to monitor network traffic in real time for any digital information that meets the user’s definition of contraband being shared using peer-to-peer protocols. The TRAPP system (see figure) is designed to be set up on the gateway between a government-owned network and the Internet. As packets pass through the gateway, copies are sent to the system for analysis. For each packet received, TRAPP inspects the packet to determine if it is a control packet for a peer-to-peer protocol of interest. If the packet is not a peer-to-peer control packet, it is discarded. If the packet is a control packet, the system extracts from the packet’s payload the unique identifier for the data being shared, and attempts to match the identifier against a list of files of interest in the system’s memory. If a match is not made, the packet is discarded. If a match is made, the control packet is recorded in a log file for future analysis.
By designing the system to be completely self-contained on a Virtex II Pro FPGA, the TRAPP system can be easily and inexpensively implemented on any local-area network (LAN), provided the system has access to a spanning port on the LAN gateway. The simplicity of the system and its FPGA-based implementation enable it to run at very high speeds, ensuring a high probability that a packet of interest is successfully intercepted, even when monitoring a heavily utilized network.
This work was done by Major Karl R. Schrader of the Air Force Institute of Technology. For more information, download the Technical Support Package (free white paper) at www.defensetechbriefs.com/tsp under the Information Sciences category. AFRL-0144
This Brief includes a Technical Support Package (TSP).

FPGA-Based System for Tracking Digital Information Transmitted Via Peer-to-Peer Protocols
(reference AFRL-0144) is currently available for download from the TSP library.
Don't have an account?
Overview
The document is a thesis by Karl R. Schrader that explores the development of an FPGA-based digital forensic tool aimed at tracking and analyzing digital information transmitted through peer-to-peer (P2P) protocols. The primary focus of the research is to address the challenges posed by illicit sharing of sensitive government data and covert communications among criminal organizations using file-sharing applications and Voice over IP (VoIP) technologies.
The thesis begins with an introduction that outlines the motivation behind the research, emphasizing the increasing prevalence of P2P protocols in data sharing and the associated risks of unauthorized data dissemination. It highlights the need for effective monitoring and forensic analysis tools to combat these threats.
A significant portion of the document is dedicated to discussing the BitTorrent peer-to-peer protocol, which is a common method for file sharing. The thesis provides an overview of the protocol's purpose, services, and typical file transfer sessions. It delves into the technical aspects of the .torrent file, the operations of the tracker protocol, and the peer wire protocol, including an analysis of the handshake packet used to extract the unique 20-byte hash of the file being transferred. Real-world examples of BitTorrent messages are examined to illustrate the practical implications of the protocol.
The document also addresses the design and implementation of the FPGA-based tool, detailing how it can effectively monitor and log file transfers and VoIP calls. The tool is designed to analyze the data packets exchanged during these sessions, enabling investigators to identify suspicious activities and gather evidence for further analysis.
In conclusion, the thesis emphasizes the importance of developing advanced digital forensic tools to enhance the capabilities of law enforcement and intelligence agencies in tracking illicit activities in the digital realm. By leveraging FPGA technology, the proposed system aims to provide a robust solution for monitoring P2P communications and ensuring the integrity of sensitive information.
Overall, Schrader's work contributes to the field of digital forensics by offering a novel approach to addressing the challenges posed by modern data-sharing technologies, ultimately aiming to protect national security and prevent the unauthorized dissemination of critical information.
Top Stories
NewsSensors/Data Acquisition
![]() Microvision Aquires Luminar, Plans Relationship Restoration, Multi-industry Push
Microvision Aquires Luminar, Plans Relationship Restoration, Multi-industry Push
INSIDERRF & Microwave Electronics
![]() A Next Generation Helmet System for Navy Pilots
A Next Generation Helmet System for Navy Pilots
INSIDERWeapons Systems
![]() New Raytheon and Lockheed Martin Agreements Expand Missile Defense Production
New Raytheon and Lockheed Martin Agreements Expand Missile Defense Production
NewsAutomotive
![]() Ford Announces 48-Volt Architecture for Future Electric Truck
Ford Announces 48-Volt Architecture for Future Electric Truck
INSIDERAerospace
![]() Active Strake System Cuts Cruise Drag, Boosts Flight Efficiency
Active Strake System Cuts Cruise Drag, Boosts Flight Efficiency
ArticlesTransportation
Webcasts
Aerospace
![]() Cooling a New Generation of Aerospace and Defense Embedded...
Cooling a New Generation of Aerospace and Defense Embedded...
Energy
![]() Battery Abuse Testing: Pushing to Failure
Battery Abuse Testing: Pushing to Failure
Power
![]() A FREE Two-Day Event Dedicated to Connected Mobility
A FREE Two-Day Event Dedicated to Connected Mobility
Automotive
![]() Quiet, Please: NVH Improvement Opportunities in the Early Design Cycle
Quiet, Please: NVH Improvement Opportunities in the Early Design Cycle
Electronics & Computers
![]() Advantages of Smart Power Distribution Unit Design for Automotive &...
Advantages of Smart Power Distribution Unit Design for Automotive &...
Unmanned Systems
![]() Sesame Solar's Nanogrid Tech Promises Major Gains in Drone Endurance
Sesame Solar's Nanogrid Tech Promises Major Gains in Drone Endurance