The Intersection of Autonomy and Cybersecurity
New automated safety features and increased connectivity require truck and off-highway OEMs to prioritize vehicle security and minimize cyber threats.
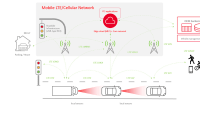
The race to greater autonomy is on in the industrial and commercial transportation industry and for good reason. Autonomous vehicles have the potential to transform commercial trucking, revolutionizing supply chain logistics, improving efficiency and lowering costs.

In today’s transportation market, around 90% of all on-highway commercial trucks use advanced driver assistance systems (ADAS), which include forward collision warning, automatic emergency braking, lane keep assist, adaptive cruise control, camera-based mirrors and blind-spot warning systems. As early as 2027, however, we could begin to see next-level autonomous trucks on our highways operating without drivers, both individually or in platoons where two, three or more trucks will operate like a road-train with only one driver in the first truck.
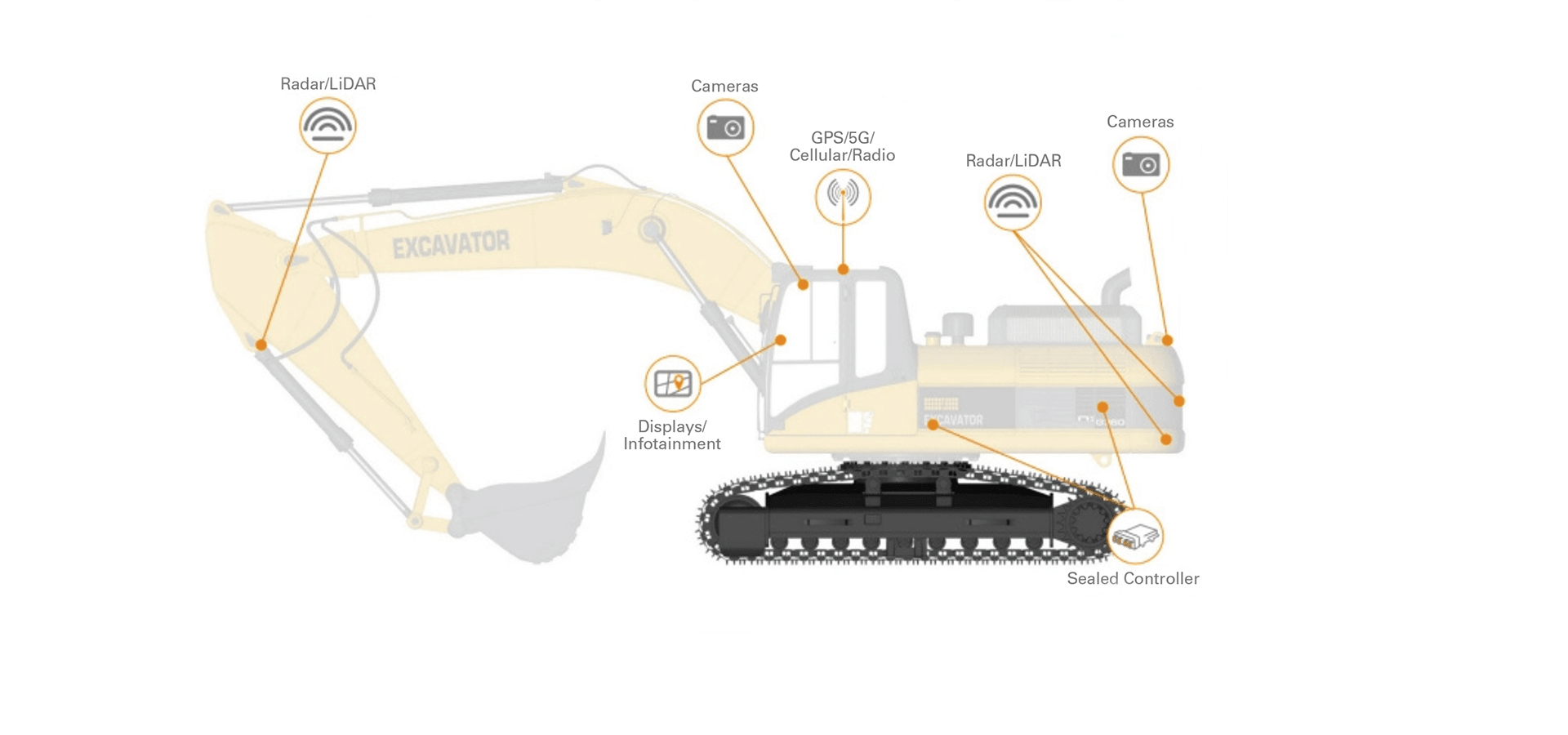
In the off-highway space, vehicles in the mining and construction industries are also leveraging some degree of automation to drive throughput and increase worker safety on the job. Both manually operated and autonomous vehicles use sensor-guided systems to make tight turns in constrained spaces, turn in unison to avoid collision and avoid rolling over.
Even with partial autonomy, safety and productivity are significantly improved when using these systems. In terms of sustainability, the increased efficiency and fuel economy delivered from semi-autonomous vehicles also delivers value by helping to reduce fuel consumption, which positively impacts both the environment and the bottom line.
Software, data and the need for cybersecurity
While the growth in autonomous vehicles is delivering significant benefits throughout the industry, this evolution is not without its challenges. The myriads of automated safety features built into today’s trucks and commercial equipment are controlled by software. And whenever software is involved, cyber vulnerabilities are a major concern.
After all, trucks move nearly 80% of intrastate goods and carry natural gas and fossil fuels, gasoline, foodstuffs, electronics, pharmaceuticals and more. They represent a target for bad actors who may seek to use the vehicle’s software to interrupt the flow of goods or worse. In the off-highway space, this scenario could mean construction projects are disrupted, or farming operations are impeded.
Autonomous functionality isn’t the only example of the exponential increase in the reliance trucks and off-highway equipment have on software and data. These vehicles are now incorporating sensors that gather data from other vehicles and even the environment itself using cameras and lidar and connecting to cloud-based platforms to enable advanced navigation and fleet management services.
As an example, on a jobsite, GPS systems with lidar and radar sensors integrate with telematics software to provide the real-time location of all machinery, while proximity and other sensors detect blind spots and the proximity of nearby equipment, information that can then be used to improve safety, productivity and performance.
Remote condition monitoring and diagnostics are also becoming more commonplace in the industry with information on the status of the vehicle or equipment being used to prevent maintenance issues before they occur.
The result of all this new technology is the creation of massive amounts of data. As this data becomes more interconnected and intertwined, the more vulnerable it becomes as well. If an attacker were to get a hold of and manipulate vehicle data, incorrect decisions could be made, operations could be impacted, or injuries could occur.
Take, for instance, an operator controlling a backhoe at a construction site who can easily avoid hitting a utility line thanks to a cloud-connected device that limits how deep the equipment can dig. If a hacker were to take control of that data or manipulate it in some way, the operator might act in error, putting themselves, bystanders, their equipment and their project at risk.
Considerations for minimizing cyber threats
While the threat that a cyberattack could compromise an entire fleet of vehicles or stall work at a jobsite is real, there are ways to minimize those risks and ensure that systems are as secure as possible. Here are a few suggestions:
Determine what’s wireless and what’s not – While using wireless sensors and antennas to capture and transmit all data internally is tempting, it creates greater risks. OEMs may consider staying wired for internal communications and using shielded copper cables and connectors for external communications.
Assess V2X communications vehicle-by-vehicle – Fast-moving autonomous vehicles, such as trucks, require V2X communications to adapt their response to changing conditions. The same holds for heavy equipment, such as construction or mining vehicles used in tight operating environments, where they need to coordinate movement and turns. These vehicles should have robust encryption protocols to protect all V2X traffic. However, slower-moving equipment, such as tractors used on farms, may be able to use less robust cellular networks if they don’t need to communicate with other vehicles or maneuver around them.

Decide what data to collect and store – Trucks and off-highway vehicles are using more and more sensors to collect data on system performance and conditions. This data is typically captured and streamed into large data lakes to enable real-time analytics. However, these cloud-based systems can have potential gaps and vulnerabilities. As a result, designers should carefully consider the data they are collecting and how long that data may be available to the end user.
Leverage advanced technology to improve security – Data analytics can uncover security gaps and vulnerabilities so that teams can address them before they impact vehicle operations. Data integrity solutions can continuously validate the authenticity of data transmitted from sensors and systems. AI-based systems can detect behavioral anomalies, such as unusual driving patterns, while adaptive security protocols can automate a corrective response, such as cutting vehicle power.
As the truck and off-highway industry continues to add new features and functionality through electronification and autonomy, vehicle security and minimizing cyber threats will need to continually be top of mind. OEMs will need to work closely with component manufacturers, connectivity providers and security system vendors to evolve security strategies, systems and processes and to ensure that their vehicles are secure, resilient and adaptive as the industry progresses forward.
Mark Brubaker, senior manager of business development, TE Connectivity, wrote this article for SAE Media.
Top Stories
NewsRF & Microwave Electronics
![]() Microvision Aquires Luminar, Plans Relationship Restoration, Multi-industry Push
Microvision Aquires Luminar, Plans Relationship Restoration, Multi-industry Push
INSIDERAerospace
![]() A Next Generation Helmet System for Navy Pilots
A Next Generation Helmet System for Navy Pilots
INSIDERDesign
![]() New Raytheon and Lockheed Martin Agreements Expand Missile Defense Production
New Raytheon and Lockheed Martin Agreements Expand Missile Defense Production
INSIDERMaterials
![]() How Airbus is Using w-DED to 3D Print Larger Titanium Airplane Parts
How Airbus is Using w-DED to 3D Print Larger Titanium Airplane Parts
NewsPower
![]() Ford Announces 48-Volt Architecture for Future Electric Truck
Ford Announces 48-Volt Architecture for Future Electric Truck
ArticlesAR/AI
Webcasts
Electronics & Computers
![]() Cooling a New Generation of Aerospace and Defense Embedded...
Cooling a New Generation of Aerospace and Defense Embedded...
Automotive
![]() Battery Abuse Testing: Pushing to Failure
Battery Abuse Testing: Pushing to Failure
Power
![]() A FREE Two-Day Event Dedicated to Connected Mobility
A FREE Two-Day Event Dedicated to Connected Mobility
Unmanned Systems
![]() Quiet, Please: NVH Improvement Opportunities in the Early Design Cycle
Quiet, Please: NVH Improvement Opportunities in the Early Design Cycle
Automotive
![]() Advantages of Smart Power Distribution Unit Design for Automotive &...
Advantages of Smart Power Distribution Unit Design for Automotive &...
Energy
![]() Sesame Solar's Nanogrid Tech Promises Major Gains in Drone Endurance
Sesame Solar's Nanogrid Tech Promises Major Gains in Drone Endurance