SIPHER: Scalable Implementation of Primitives for Homomorphic Encryption
Improving the efficiency and scalability of Fully Homomorphic Encryption (FHE).
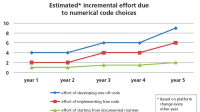
Prior to the Proceed program, the main challenges preventing practical demonstrations and use of Fully Homomorphic Encryption (FHE) were efficiency and scalability. At the start of the Program, the state-of-the-art FHE implementations were both inefficient and not scalable. Work in Scalable Implementation of Primitives for Homomorphic EncRyption (SIPHER) has brought FHE into the realm of practice, bringing several orders of magnitude runtime improvement, and resulting in FHE implementations that can be executed on single and multicore computers (including iPhones). Furthermore, implementation of an FHE hardware accelerator on a Virtex 7 Field Programmable Gate Array (FPGA) can speed up core FHE functions by over three orders of magnitude.
Previous FHE schemes were inefficient because the underlying algorithms and their implementations took too long to run at an appropriate level of assured security. Similarly, these FHE schemes were not scalable because memory requirements for encrypting practical-length messages with a reasonable level of security exceed the abilities of highly parallel computation devices like FPGAs. These issues are driven by several factors:
- The very large keys required for an assured level of security and large expansion of unencrypted plaintext messages to encrypted ciphertext.
- The large computation depth needed for Bootstrapping/Recryption circuits (an efficiency bottleneck of FHE schemes).
- The lack of scalable and highly optimized implementations of basic modulus ring operations, which are building blocks used across many lattice FHE schemes.
These activities culminated in many orders of magnitude improvement for these bottlenecks. This revolutionary improvement was achieved by significantly advancing the state of the art in a number of independent focus areas:
- Multiple foundational improvements in the underlying FHE scheme for more efficient and scalable implementations of FHE operations. These improvements include a new approach to FHE Recryption, and the use of modulus and ring reduction to limit ciphertext expansion.
- Parallelizable, efficient algorithm design for scalable implementations of basic computational primitives at the core of lattice FHE schemes improving runtime of all FHE operations.
- Advanced code development approach for efficient and flexible embedded and FPGA implementations.
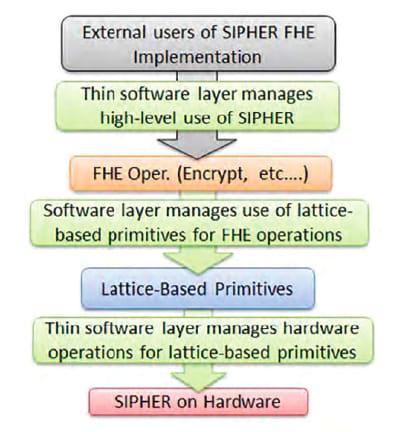
The accompanying Figure shows the layered SIPHER approach. Software interfaces are provided for optimized basic FHE operations. This lets users construct general applications computing on encrypted data. Core lattice-based primitives form the heart of the FHE implementations. This modular approach allows users to:
- construct and experimentally modify multiple implementations of FHE operations and
- easily deploy code on FPGA hardware to run the primitives on cost-effective, massively parallel hardware, providing 3 orders of magnitude improvement in basic FHE operation runtimes.
This work was done by David Cousins, Kurt Rohloff, Christopher Peikert, and Daniel Sumorok of Raytheon BBN Technologies for the Air Force Research Laboratory. AFRL-0244
This Brief includes a Technical Support Package (TSP).

SIPHER: SCALABLE IMPLEMENTATION OF PRIMITIVES FOR HOMOMORPHIC ENCRYPTION
(reference AFRL-0244) is currently available for download from the TSP library.
Don't have an account?
Overview
The document discusses threshold cryptographic schemes, focusing on their properties, security, and protocols. A threshold cryptographic scheme allows a group of trustees to perform privileged operations collectively, requiring a minimum number of honest parties (denoted as h) to ensure security and correctness, even if some parties (up to t, where t < h) act adversarially. This setup is crucial for maintaining robustness in cryptographic protocols, particularly in environments where secure erasures cannot be guaranteed.
The paper emphasizes the importance of information-theoretic security, which provides statistical security against adaptive corruptions. This means that the protocols are designed to withstand attacks where adversaries can adapt their strategies based on the information they gather during the execution of the protocol. The authors highlight that their protocols are structured to ensure that commands issued by the environment are always directed towards at least h honest parties in the same round, reinforcing the integrity of the operations performed.
Additionally, the document touches on the learning with errors (LWE) problem, which is a foundational concept in modern cryptography. The LWE problem involves distinguishing between certain distributions that are perturbed by noise, and it has significant implications for the security of cryptographic systems. The authors explore the implications of this problem in the context of their proposed protocols and the overall security framework.
The document also references the Short Integer Solution (SIS) problem, which is closely related to LWE and is used in constructing secure cryptographic primitives. The authors argue that their approach to threshold cryptography, combined with the principles of LWE and SIS, leads to robust and secure protocols that can be applied in various cryptographic applications.
In summary, the document provides a comprehensive overview of threshold cryptographic schemes, their security properties, and the underlying mathematical problems that support their robustness. It emphasizes the need for protocols that can withstand adversarial actions while ensuring that a sufficient number of honest parties are involved in the decision-making process, thereby maintaining the integrity and security of cryptographic operations.
Top Stories
INSIDERDefense
![]() New Raytheon and Lockheed Martin Agreements Expand Missile Defense Production
New Raytheon and Lockheed Martin Agreements Expand Missile Defense Production
NewsAutomotive
![]() Ford Announces 48-Volt Architecture for Future Electric Truck
Ford Announces 48-Volt Architecture for Future Electric Truck
INSIDERManufacturing & Prototyping
![]() Active Strake System Cuts Cruise Drag, Boosts Flight Efficiency
Active Strake System Cuts Cruise Drag, Boosts Flight Efficiency
ArticlesTransportation
![]() Accelerating Down the Road to Autonomy
Accelerating Down the Road to Autonomy
INSIDERMaterials
![]() How Airbus is Using w-DED to 3D Print Larger Titanium Airplane Parts
How Airbus is Using w-DED to 3D Print Larger Titanium Airplane Parts
Road ReadyTransportation
Webcasts
Electronics & Computers
![]() Cooling a New Generation of Aerospace and Defense Embedded...
Cooling a New Generation of Aerospace and Defense Embedded...
Power
![]() Battery Abuse Testing: Pushing to Failure
Battery Abuse Testing: Pushing to Failure
Connectivity
![]() A FREE Two-Day Event Dedicated to Connected Mobility
A FREE Two-Day Event Dedicated to Connected Mobility
Automotive
![]() Quiet, Please: NVH Improvement Opportunities in the Early Design Cycle
Quiet, Please: NVH Improvement Opportunities in the Early Design Cycle
Transportation
![]() Advantages of Smart Power Distribution Unit Design for Automotive &...
Advantages of Smart Power Distribution Unit Design for Automotive &...
Aerospace
![]() Sesame Solar's Nanogrid Tech Promises Major Gains in Drone Endurance
Sesame Solar's Nanogrid Tech Promises Major Gains in Drone Endurance