Managing Security in FPGA-Based Embedded Systems
FPGAs used in encryption, avionics, computer vision, wireless networks, intrusion detection systems, and supercomputers require strong security.
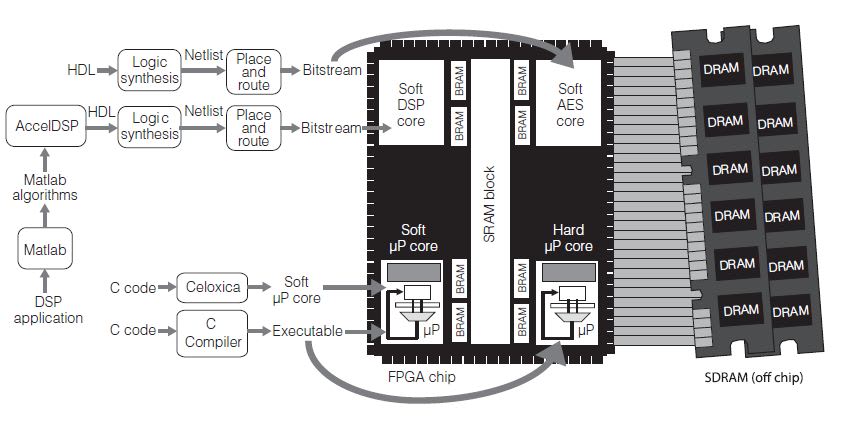
Field-programmable gate arrays (FPGAs) combine the programmability of processors with the performance of custom hardware. As they become more common in critical embedded systems, new techniques are necessary to manage security in FPGA designs. Because FPGAs can provide a useful balance between performance, rapid time to market, and flexibility, they have become the primary source of computation in many critical embedded systems. However, techniques beyond bitstream encryption are necessary to ensure FPGA design security.
FPGAs are a natural platform for the implementation of cryptographic algorithms, given the large number of bit level operations required in modern block ciphers. Because transformations also require shifting or permuting bits, these operations can be wired into the FPGA, thus incurring extremely low overhead, and with parallelism where appropriate. The subversion of design tools could easily result in malicious design being loaded onto a device. For example, a malicious design could physically destroy the FPGA by causing the device to short circuit. In fact, major design-tool developers have few or no checks in place to ensure that attacks on specific functionality are not included.
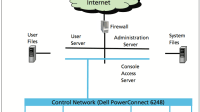
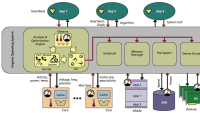
Industry needs a holistic approach to manage security in FPGA-based embedded- systems design. Systems can be composed at the device, board, and network levels. This approach to secure system composition on an FPGA employs many different techniques, both static and runtime, including lifecycle management, reconfigurable mechanisms, spatial isolation, and a coherent security architecture. A successful security architecture must help designers manage system complexity without requiring all system developers to have complete knowledge of the inner workings of all hardware and software components, which are far too complex for complete analysis. An architecture that enables the use of both evaluated and unevaluated components would let one build systems without having to reassess all the elements for every new composition.
Most prior work relating to FPGA security focuses on preventing IP theft and securely uploading bitstreams in the field. Industry has already developed several techniques to combat FPGA IP theft, such as encryption, fingerprinting, and watermarking. However, establishing a root of trust on a fielded device is challenging because it requires incorporating a decryption key into the finished product. Some FPGAs can be remotely updated in the field, and industry has devised secure hardware update channels that use authentication mechanisms to prevent a subverted bitstream from being uploaded. These techniques were developed to prevent an attacker from uploading a malicious design that causes unintended functionality.
A strategy is needed for lifecycle protection of hardware to provide accountability in the development process, including control of the development environment and tools, as well as trusted delivery of the chips from the factory. Both cores and tools should be placed under a configuration management system. Ideally, it should be possible to verify that the output of each stage of the design flow faithfully implements the input to that stage through the use of formal methods such as model checking.
An alternative is to build a custom set of trusted tools for security-critical hardware. This tool chain would implement a subset of the commercial tool chain’s optimization functions, and the resulting designs would likely sacrifice some measure of performance for additional security. Existing research on trusted compilers could be exploited to minimize the development effort. A critical function of lifecycle protection is to ensure that the output (and transitively, the input) does not contain malicious artifacts. Testing can also help ensure fidelity to requirements and common failure modes. For example, it should consider the location of the system’s entry points, its dependencies, and its behavior during failure.
Lifecycle management also includes delivery and maintenance. Trusted delivery ensures that the FPGA has not been tampered with from manufacturing to customer delivery. For an FPGA, maintenance includes updates to the configuration, which can occur remotely on some FPGAs. For example, a vendor might release an improved version of the bitstream that fixes bugs in the earlier version.
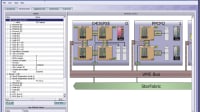
Programmability of FPGAs is a major advantage for providing on-chip security, but this malleability introduces unique vulnerabilities. Industry is reluctant to add security features to ASICs, because the edit-compile-run cycle cost can be prohibitive. FPGAs, on the other hand, provide the opportunity to incorporate self-protective security mechanisms at a far lower cost.
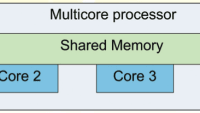
One example of a runtime security mechanism that can be built into reconfigurable hardware is memory protection. On most embedded devices, memory is flat and unprotected. A reference monitor, a well-understood concept from computer security, can enforce a policy that specifies the legal sharing of memory (and other computing resources) among cores on a chip. A reference monitor is an access control mechanism that possesses three properties: it is self-protecting, its enforcement mechanisms cannot be bypassed, and it can be subjected to analysis that ensures its correctness and completeness. Reference monitors are useful in composing systems because they are small and do not require any knowledge of a core’s inner workings.
This work was done by Ted Huffmire, Timothy Levin, Thuy D. Nguyen, and Cynthia Irvine of the Naval Postgraduate School; Brett Brotherton of Special Technologies Laboratory; Timothy Sherwood of the University of California, Santa Barbara; and Ryan Kastner of the University of California, San Diego. NRL-0058
This Brief includes a Technical Support Package (TSP).

Managing Security in FPGA-Based Embedded Systems
(reference NRL-0058) is currently available for download from the TSP library.
Don't have an account?
Overview
The document discusses the challenges and advancements in managing security within FPGA-based embedded systems, particularly in critical applications such as aerospace and military sectors. It emphasizes the growing importance of hardware security as embedded systems become more complex and interconnected. The authors highlight that traditional security measures, such as bitstream encryption, are insufficient to address the multifaceted security threats faced by these systems.
The document outlines the need for a holistic approach to system design that incorporates security considerations throughout the development lifecycle. It advocates for the adaptation of software development security practices to hardware design, ensuring that security is integrated from the ground up. This includes the use of life-cycle management tools and techniques that have been established for trustworthy software development.
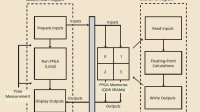
Key topics covered include the concept of partial reconfiguration in FPGAs, which allows for dynamic updates to the system while it is operational. This capability is particularly valuable in applications like avionics, where systems may need to be updated in-flight for fault tolerance. However, the document notes that implementing secure partial reconfiguration is complex, as it requires maintaining secure states across updates and ensuring that new configurations do not introduce vulnerabilities.
The authors also discuss the risks associated with shared resources in multi-domain systems, such as covert channels that can leak sensitive information between different security domains. They propose the development of formal and practical methods to manage these risks, including the use of spatial and temporal schemes to enforce security policies.
Furthermore, the document highlights the importance of trusted components within a system, especially when dealing with sensitive data. It suggests that certain functions, such as authentication, must reside in a trusted core to ensure a high degree of trustworthiness.
Overall, the document serves as a call to action for practitioners in the field to enhance their understanding of security implications in FPGA design and to adopt a more rigorous approach to security in the development of embedded systems. By doing so, they can better protect against emerging threats and ensure the integrity and reliability of their systems.
Top Stories
INSIDERDefense
![]() New Raytheon and Lockheed Martin Agreements Expand Missile Defense Production
New Raytheon and Lockheed Martin Agreements Expand Missile Defense Production
NewsAutomotive
![]() Ford Announces 48-Volt Architecture for Future Electric Truck
Ford Announces 48-Volt Architecture for Future Electric Truck
INSIDERManufacturing & Prototyping
![]() Active Strake System Cuts Cruise Drag, Boosts Flight Efficiency
Active Strake System Cuts Cruise Drag, Boosts Flight Efficiency
ArticlesTransportation
![]() Accelerating Down the Road to Autonomy
Accelerating Down the Road to Autonomy
INSIDERMaterials
![]() How Airbus is Using w-DED to 3D Print Larger Titanium Airplane Parts
How Airbus is Using w-DED to 3D Print Larger Titanium Airplane Parts
Road ReadyTransportation
Webcasts
Electronics & Computers
![]() Cooling a New Generation of Aerospace and Defense Embedded...
Cooling a New Generation of Aerospace and Defense Embedded...
Power
![]() Battery Abuse Testing: Pushing to Failure
Battery Abuse Testing: Pushing to Failure
Connectivity
![]() A FREE Two-Day Event Dedicated to Connected Mobility
A FREE Two-Day Event Dedicated to Connected Mobility
Automotive
![]() Quiet, Please: NVH Improvement Opportunities in the Early Design Cycle
Quiet, Please: NVH Improvement Opportunities in the Early Design Cycle
Transportation
![]() Advantages of Smart Power Distribution Unit Design for Automotive &...
Advantages of Smart Power Distribution Unit Design for Automotive &...
Aerospace
![]() Sesame Solar's Nanogrid Tech Promises Major Gains in Drone Endurance
Sesame Solar's Nanogrid Tech Promises Major Gains in Drone Endurance