Cyber Security Goes Upstream
The first cloud-based solution for connected vehicles was born in Israel and is now pilot-testing at global OEMs.

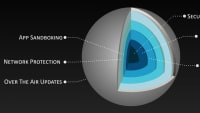
What can hackers do with a car? Just about anything they want. A typical vehicle today is a potential sitting duck, cybersecurity experts say. They point to ghosted schematics of cars showing dozens of ‘attack vectors’ — the places that are in various ways vulnerable to security intrusions.
Lock the doors of your former boss’s F-150 remotely, for spite and kicks? Too easy. How about something a bit more ambitious — like locking the doors in F-150s across the state and keeping them locked for an hour? Angry owners might diss Ford, but the fallout would be minor compared to the damage and pain inflicted by a remote hack of vehicle brakes or steering. Or a mass hack involving ransomware.
“We work with a lot of ‘white hat’ guys, one of whom is ‘the LeBron James’ of car hackers,” noted Dan Sahar, VP of Product for Israel-based Upstream Security. “Ask him how to secure at the vehicle level and he’ll tell you it’s impossible. The electronic throttle control, the powertrain ECU — when was the code written for these? The OEMs often don’t have control, and they share many suppliers and components,” asserted Sahar, a computer scientist.
“If one of the Tier 1 electronic-systems integrators makes a mistake regarding security, everyone can get hit,” he said. “The industry has rapidly moved from having zero security problems to a world in which very bad things can happen, not only to an enterprise and an IT organization, but physical damage to people.”
Infinite processing power
The danger becomes exponential with an estimated 200 million connected and increasingly automated vehicles expected to be in use by early next decade, Sahar said in an interview with Autonomous Vehicle Engineering. They’ll be exposed to even more new threats. Security attacks on vehicle fleets including MaaS (mobility as a service) providers, delivery companies and those leased by businesses and government agencies are likely to increase, Sahar and other experts believe.
“The second you enable connectivity, you increase the threat level dramatically. That’s the risk,” he said. How, then, does an enterprise protect itself ? Applying the security layer inside the car will always put connected vehicles steps behind the hackers and more vulnerable to the most recent threats, Sahar argued. The optimum place for security instead is in the cloud, reckoned former Israeli Defense Forces cybersecurity veterans Yonatan Appel and his colleague Yoav Levy when they founded Upstream nearly two years ago.
“We’re the only company in the automotive cyber space that places the security in the cloud — between the car, the telematics server and the mobile-applications server,” Sahar explained. “The others still pursue the in-vehicle path. If you firewall something it will be obsolete in two years. CPUs get old.
“But in the cloud, I have infinite processing. If I need more power I just add more servers. And the defenses can be updated remotely with new code. You can’t do that by putting code in the car.”
The formidable data-collecting ability of future connected vehicles is a potential pot of gold for OEMs and Sahar sees significant opportunities for his company, which has grown to nearly 40 employees in 2018.
Preventing rogue attacks
“Data generation and collection per vehicle will be enormous. The industry moving to 5G is good for us — more data and more risk in terms of security threats. And this benefits the effectiveness of our centralized position in the cloud where we can monitor every bit of traffic that goes on there,” he explained. “We map out what’s normal traffic and what’s not,” using Upstream’s artificial intelligence, machine learning and advanced data-analytics tools.
Sahar cites a real-world detection example: “If we see an OTA update sent to the car without authentication, followed by an ‘OTA update complete’ response from the car, we flag it. Who told it to do an update? We’ve seen these events — they’re rogue attacks,” he said. “The aim is to detect and prevent threats before the reach they network.”
More data from more OEMs that Upstream monitors means more effective security solutions, according to Sahar. “The global makers all use components from the same Tier 1s. The hardware in many cases is similar. If we found a security anomaly in one area of a BMW, for example, we’d then apply it on others.”
Upstream monitoring also could spot anomalies in MaaS activities — for example, fraudulent use of rental vehicles based on the data footprint.
Upstream currently has nearly a dozen OEM customers, some using the product in advanced-pilot stage, as well as MaaS fleets in North America, Europe and Israel. Last spring, the company entered a strategic partnership with Asgent, a Tokyo-based developer and distributor of network security to provide automotive cybersecurity solutions to OEMs and vehicle fleets in Japan.
“The industry now has a deadline to ship connected cars within a few years. They have to get the security done,” Sahar opined. “Autos is a cat-and-mouse game and the security holes are big and easy to penetrate. We’re in the process of changing that,” he said.
Top Stories
INSIDERDefense
![]() New Raytheon and Lockheed Martin Agreements Expand Missile Defense Production
New Raytheon and Lockheed Martin Agreements Expand Missile Defense Production
NewsAutomotive
![]() Ford Announces 48-Volt Architecture for Future Electric Truck
Ford Announces 48-Volt Architecture for Future Electric Truck
INSIDERManufacturing & Prototyping
![]() Active Strake System Cuts Cruise Drag, Boosts Flight Efficiency
Active Strake System Cuts Cruise Drag, Boosts Flight Efficiency
ArticlesTransportation
![]() Accelerating Down the Road to Autonomy
Accelerating Down the Road to Autonomy
INSIDERMaterials
![]() How Airbus is Using w-DED to 3D Print Larger Titanium Airplane Parts
How Airbus is Using w-DED to 3D Print Larger Titanium Airplane Parts
Road ReadyTransportation
Webcasts
Electronics & Computers
![]() Cooling a New Generation of Aerospace and Defense Embedded...
Cooling a New Generation of Aerospace and Defense Embedded...
Power
![]() Battery Abuse Testing: Pushing to Failure
Battery Abuse Testing: Pushing to Failure
Connectivity
![]() A FREE Two-Day Event Dedicated to Connected Mobility
A FREE Two-Day Event Dedicated to Connected Mobility
Automotive
![]() Quiet, Please: NVH Improvement Opportunities in the Early Design Cycle
Quiet, Please: NVH Improvement Opportunities in the Early Design Cycle
Transportation
![]() Advantages of Smart Power Distribution Unit Design for Automotive &...
Advantages of Smart Power Distribution Unit Design for Automotive &...
Aerospace
![]() Sesame Solar's Nanogrid Tech Promises Major Gains in Drone Endurance
Sesame Solar's Nanogrid Tech Promises Major Gains in Drone Endurance