Addressing Configuration Controls in an Era of Multiple Security Frameworks
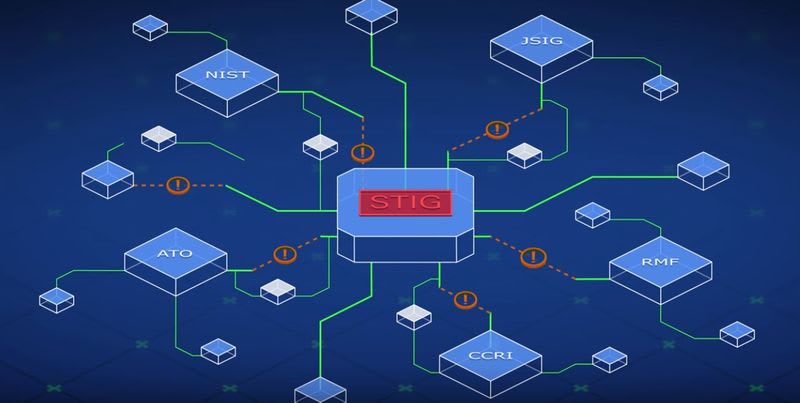
We have entered the era of multiple security frameworks . Sometimes mandatory, often voluntary, security frameworks are created to provide federal and commercial organizations with an effective roadmap for securing information technology (IT) systems. The goal is to reduce risk levels and prevent or mitigate cyberattacks.
To accomplish this task, security frameworks typically provide a series of documented, agreed upon, and understood policies, procedures, and processes necessary to secure the confidentiality, integrity, and availability of information systems and data.
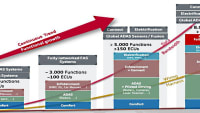
If a drawback to security frameworks exists, however, it is that most provide a “30,000-foot view” of information security. Most identify potential risks as well as how to protect, detect, respond, and even recover from cyberattacks. Specific implementation steps, on the other hand, are rarely addressed.
One critical exception exists. At the core of most, if not all, the frameworks are a set of security-related controls that affect the security posture and/or functionality of the system.
Top Stories
NewsRF & Microwave Electronics
![]() Microvision Aquires Luminar, Plans Relationship Restoration, Multi-industry Push
Microvision Aquires Luminar, Plans Relationship Restoration, Multi-industry Push
INSIDERAerospace
![]() A Next Generation Helmet System for Navy Pilots
A Next Generation Helmet System for Navy Pilots
INSIDERDesign
![]() New Raytheon and Lockheed Martin Agreements Expand Missile Defense Production
New Raytheon and Lockheed Martin Agreements Expand Missile Defense Production
INSIDERMaterials
![]() How Airbus is Using w-DED to 3D Print Larger Titanium Airplane Parts
How Airbus is Using w-DED to 3D Print Larger Titanium Airplane Parts
NewsPower
![]() Ford Announces 48-Volt Architecture for Future Electric Truck
Ford Announces 48-Volt Architecture for Future Electric Truck
ArticlesAR/AI
Webcasts
Electronics & Computers
![]() Cooling a New Generation of Aerospace and Defense Embedded...
Cooling a New Generation of Aerospace and Defense Embedded...
Automotive
![]() Battery Abuse Testing: Pushing to Failure
Battery Abuse Testing: Pushing to Failure
Power
![]() A FREE Two-Day Event Dedicated to Connected Mobility
A FREE Two-Day Event Dedicated to Connected Mobility
Unmanned Systems
![]() Quiet, Please: NVH Improvement Opportunities in the Early Design Cycle
Quiet, Please: NVH Improvement Opportunities in the Early Design Cycle
Automotive
![]() Advantages of Smart Power Distribution Unit Design for Automotive &...
Advantages of Smart Power Distribution Unit Design for Automotive &...
Energy
![]() Sesame Solar's Nanogrid Tech Promises Major Gains in Drone Endurance
Sesame Solar's Nanogrid Tech Promises Major Gains in Drone Endurance