To Serve and Protect
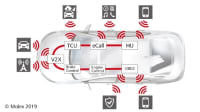
As cars become more connected and automated, cybersecurity concerns are rising. Industry engineers have many tools and techniques and are now deploying encryption and standards to ensure that vehicle controls are not altered or usurped by unauthorized people.

Automotive security concerns have rapidly evolved from physical equipment like door locks to cybersecurity concerns for connected vehicles. Developers are now deploying encryption, standards, and other techniques in their battles to ensure that vehicle controls are not altered or usurped by unauthorized people.
Connectivity’s growth means increases in the number of potential points for breaches, which extends the complexity of security systems. Design teams have to safeguard not only vehicle systems but also the links to cell phones and other devices. Many developers have set a high bar for prevention, feeling that no dangerous intrusion should occur.
“I don’t know that you want to allow a hack that can cause something disastrous; you have to set the target at zero,” said Andrew Poliak, Global Director, Business Development, for QNX Software Systems. “It’s not a foregone conclusion that vehicles will be hacked, at least in a way that will cause safety problems.”
That’s a big challenge. Figuring out who, or what, can access controllers and write or alter code in them is no simple task. The risks come from humans and the loosely defined group of servers that make up the Cloud.
“You need to ensure secure access with controls so only authorized entities have access,” said Timo van Roermund, Security Architect at NXP Semiconductors. “Many people think that’s only confidentiality, but authentication must be considered. If the Cloud wants to access a vehicle system, it needs to authenticate itself first.”
Tight links between cell phones and vehicle electronics further complicate the challenge. Portable devices infected with sophisticated malware will be connected to infotainment systems that may share the networks used by many other controllers.
“As traditional enterprises and businesses have had to adopt a bring-your-own-device management strategy, the connected vehicle will be influenced in much the same way,” said Mike Weber, Vice President of Coalfire Labs. “The demand for technology in the vehicle will not only be driven by the partner vendors that feed data to and consume data from the vehicle, but also by the expectations of integration of personal devices.”
Many tools and techniques

Preventing hackers from getting into vehicle systems requires a range of technologies that span the development cycle. Multiple techniques must be layered in a comprehensive strategy that addresses various threats. Encryption, one of the basic protective techniques, requires safely storing the keys used to encode and decode data sent across the network.
“The encryption of data, for instance by means of asymmetric cryptography using the public/private key principle, is a fundamental prerequisite for modern, in-vehicle security solutions,” said Walter Sullivan, Head of Elektrobit’s Silicon Valley Innovation Lab. “The encryption of data and transmission paths is based on signatures, whereby one key is publicly accessible (public) and the other is known only to the user or component (private).”
The software used to enhance security further increases the need for tools that speed the development and testing of code. All hardware and software must be checked from the initial steps through the final integration with all equipment on the vehicle, then when mobile devices are linked to the auto.
“The addition of security and intruder safeguards is another factor that contributes to the exponentially growing amount of embedded software found in vehicles today,” said Nicholas Keel, Group Manager of Real-Time Test Marketing at National Instruments. “To support these new challenges, design and test tools used to develop and verify embedded systems must evolve to improve efficiency and increase collaboration across different groups in an organization.”
The rapid expansion of software is matched by consumer expectations of instant responses. That drives the demand for faster microcontrollers and memories, though speed increases come with higher power requirements.
“There are many tradeoffs around boot speeds and CPU utilization; people don’t want to wait a minute for their car to boot up,” Poliak said. “Power consumption is also an issue. Cell phones check for updates regularly, but they’re charged every day or so. You can’t leave your car at the airport a couple weeks and have it drain the battery while it’s downloading updates.”
No golden standard
A broad range of standards are among the tools that help engineers design for security. Standards organizations around the globe have focused on security, using the collective brainpower of users and suppliers to come up with techniques and technologies that meet the needs of different users. No single specification meets all needs, but collectively they provide an environment that is flexible enough to meet current demands and change as time marches forward.

“You need cryptographic agility,” van Roermund said. “A car is on the road 10 or more years. What’s secure today will not be secure in the future. Standards help future-proof the system, in the sense that the protocols have been designed to allow for updates.”
These standards span the gamut, from cryptographic techniques to safety functions to automotive standards like Automotive Open System Architecture (Autosar).
“Existing Autosar architectures feature proven safety mechanisms which can be used to design ECUs under functional safety and IT security requirements,” Sullivan said. “To address common security requirements, appropriate use cases can be extended with modules such as Autosar SecOC (Secure Onboard Communication), which consists of protection components for bus communication via Ethernet technology.”
Many developers note that the industry’s use of functional safety standards helps improve security. When faults are eliminated, systems are safer and easier to protect. A growing number of projects now include security in their risk assessment processes.
“A safety standard like ISO 26262 requires each function/capability of a vehicle to go through risk and hazard assessment to understand the impact on safety for passengers,” Keel said. “This means that even though a component may not initially seem to be safety-related, it still must be evaluated for all possibilities. And this includes security of all components and understanding what could happen if that security is breached.”
Top Stories
INSIDERManufacturing & Prototyping
![]() How Airbus is Using w-DED to 3D Print Larger Titanium Airplane Parts
How Airbus is Using w-DED to 3D Print Larger Titanium Airplane Parts
INSIDERManned Systems
![]() FAA to Replace Aging Network of Ground-Based Radars
FAA to Replace Aging Network of Ground-Based Radars
NewsTransportation
![]() CES 2026: Bosch is Ready to Bring AI to Your (Likely ICE-powered) Vehicle
CES 2026: Bosch is Ready to Bring AI to Your (Likely ICE-powered) Vehicle
NewsSoftware
![]() Accelerating Down the Road to Autonomy
Accelerating Down the Road to Autonomy
EditorialDesign
![]() DarkSky One Wants to Make the World a Darker Place
DarkSky One Wants to Make the World a Darker Place
INSIDERMaterials
![]() Can This Self-Healing Composite Make Airplane and Spacecraft Components Last...
Can This Self-Healing Composite Make Airplane and Spacecraft Components Last...
Webcasts
Defense
![]() How Sift's Unified Observability Platform Accelerates Drone Innovation
How Sift's Unified Observability Platform Accelerates Drone Innovation
Automotive
![]() E/E Architecture Redefined: Building Smarter, Safer, and Scalable...
E/E Architecture Redefined: Building Smarter, Safer, and Scalable...
Power
![]() Hydrogen Engines Are Heating Up for Heavy Duty
Hydrogen Engines Are Heating Up for Heavy Duty
Electronics & Computers
![]() Advantages of Smart Power Distribution Unit Design for Automotive...
Advantages of Smart Power Distribution Unit Design for Automotive...
Unmanned Systems
![]() Quiet, Please: NVH Improvement Opportunities in the Early Design...
Quiet, Please: NVH Improvement Opportunities in the Early Design...